Cisco Anyconnect Local Lan Access

I know little about Cisco VPN equipment. what I do know is that it is possible to disable client local network access, preventing the client from enabling it. I understand the security issues, but I already have a firewall in place at home and this policy is preventing me from working effectively when at home. In order to print anything to my home network printer, or access any files on my personal file server, I have to disconnect from the VPN.
I'll first request that this policy be removed just for my account, but I'd like to know first from the Ars Hive-Mind whether it's possible to do that. If I can't get that to work, I need to know how to hack the client to ignore that setting. This is something I need to get work done and (forgive my arrogance), after nearly seven years in IT, I don't think I'm a potential security hazard.
Cisco Anyconnect Local Lan Access Mac
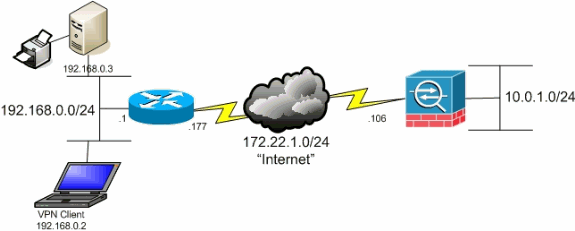
In order to access the enterprise intranet remotely, we have to use the Cisco AnyConnect VPN client. We're allowed to install it on any personal machines, and they provide downloads and instructions for Windows, Mac and Linux. This works fine except for the routing table configurations they provide. Both are using NAT/Shared network configuration. I then did an ipconfig /all on both VMs to compare. On both VMs, the 'Cisco AnyConnect Secure Mobility Client Virtual Miniport Adapter for Windows x64' shows up, and are basically identical aside from IPV6 address,. The AnyConnect VPN client can be configured to permit access to the local LAN network, in order to access local resources such as a local network printer or NAS. This relies on the configuration for excludespecified as above. Modify the ACL (created above for Split Tunnel Exclude) in order to allow local LAN access. Cisco AnyConnect Client is the only software client by Cisco that should be used now. The underlying transport can be either SSL or IPSec, but in any case this configuration is done at the VPN head-end. To be more precise, let’s say that we want to provide access to the network 10.195.1.0/24 for the customers.

