Meraki MX Technical Deep Dive (Module 3) - UTM - Duration: 39:39. How to Fix Meraki L2TP VPN Client Connection Issues - Duration: 5:04. Helpful Toots 3,025 views. Setup and configure user MX Security Appliances for VPN access using Meraki's Client VPN OS Configuration page. Note: A VPN connection can be established to the MX Security Appliance using standard VPNclient software that is included with supported Windows® operating systems, Apple® operating systems, or Android™ operating systems.
Cisco Meraki uses the integrated Windows client for VPN connection (no Cisco client at this time).
To be able to connect with simple AD user account credentials, along with a simple pre-shared key, the steps are very simple.
9 Steps total
Step 1: Get started
Click on Start and type in VPN, click on Change Virtual Private Networks (VPN)
Step 2: Add connection
Click on Add a VPN connection
Step 3: Configure Windows connection
Pick VPN provider as Windows
Name the connection
Put in server name or IP
Switch VPN type to L2TP/IPsec with pre-shared key
Switch Type of sign in to User name and password
Enter the username and password if you want to save it, or leave blank and user will have to enter it on connection
Hit Save
Step 4: Edit settings
Once you hit Save, it will bring you back to the connection page
Click on Change Adapter Options
Step 5: Configure adapter
In the adapter window, click on the adapter with the name you created in the VPN window
Click on Change settings of this connection
Step 6: Step 6
Click on Security tab
Make sure Type of VPN is still Layer 2 Tunneling Protocol with IPsec
Set Data encryption to Require encryption (disconnect if server declines)
Set Allow these protocols
Check Unencrypted password (PAP) - will still be, so don't worry
Click Advanced settings
Step 7: Add key
In the Advanced settings, click on Use preshared key
Type in the key you want to use
Hit OK to go back to the adapter settings
Click OK to close the adapter settings and save.
Close all other windows at this point.
Step 8: Connect
Connect ...
Click on the network icon in the system tray
Click on the VPN network connection name
Click on Connect
Step 9: Verify and disconnect
Verify you are connected
Click on the network system tray icon again if the window closed or minimized
You should now see the VPN network name listed and Connected underneath it
(If you are done with your connection, click on it and click Disconnect)
Now and then Windows Updates breaks the encryption settings by changing from PAP to MS-CHAP. If users could connect before, but suddenly can't while others can, revisit Step# 6 and verify PAP is turned on, not MS-CHAP. Save and all set!
8 Comments
- ChipotleBMG_Zone Jun 20, 2018 at 12:42pm
I have a customer who is stating:
We've run into a weird problem where the built in Windows 10 vpn gets its settings changed whenever the wifi network changes. We have consultants who travel to various client sites and every time they try to connect to our vpn server they have to fix their vpn settings. The company we had hired to set up our vpn server said they can't help us with this, probably because it's a Windows issue
Any Ideas?
- HabaneroKrasimirPetrov_ Oct 31, 2018 at 02:46am
Good read. Thank you very much for sharing.
Excellent tutorial - SonoraLRSpartan Jan 8, 2019 at 04:49pm
We have been trying to overcome the same problems with MX64 and making an outbound rule entry in Windows Defender Firewall is what helped us. We had performed all the other instructions Meraki and MSFT had provided including the regedit (asumeUDPEncap...).
We created a UDP port rule for 500, 4500 and scoped it to our vpn IP address. Finally works.
I hope this helps.
- Pimientoericguth2 Jan 28, 2020 at 09:00am
LRSpartan - are you saying that you port forward UDP 500 and 4500 to your VPN range 192.168.XXX.00/24?
- PoblanoAaronTheYoung Feb 3, 2020 at 08:15pm
We are constantly plagued by our VPN connection losing its settings as well. I'm not sure if this it relates to change in WiFi, but the people that it occurs with do seem to be people that change WiFi often. Others who are using it from one network at home seem to not have the issue.
In any case, I am constantly connecting to users who are remote and fixing their settings. Either resetting their Username and Password settings or fixing the PAP/CHAP protocol settings.
Is there a way to use the Powershell command ADDVPNConnection to create a script that would re-create the settings in one fell swoop?
Any help would be appreciated.
- Datiltroberts2 Mar 4, 2020 at 08:22pm
We have seen those same settings and we hear there may be a Meraki VPN Client or Cisco AnyConnect Client that is Meraki compatible in the near future, but that has also been ongoing for like 3 to 4yrs now. Once it comes out, should be a moot point on Microsponge changing your settings. I have seen the same issue though, seems to be mostly tied to Microsoft and the firewall flipping the network to public and effectively blocks like everything so you can't connect. Only way we have gotten it to work is when on that network, switch it from Public to Private, reboot the machine and possibly also the network router you are using and then it works, and yes you are sharing when connected initially to that network, but once on the VPN, tunneled into your network and secure again. Fingers X'd on the client coming out vs WinDoze client.
- Pimientospicehead-hu3x0 Apr 14, 2020 at 06:09pm
The Dreytek VPN client works for the meraki, I hope Cisco comes out with their own soon.
- Jalapenobranchms Jan 21, 2021 at 10:04pm
I'm having nothing but trouble getting this to connect.
Using windows 10 and Meraki MX64.Can you suggest a resolution?
This article outlines instructions to configure a client VPN connection on commonly-used operating systems. For more information about client VPN, please refer to our Client VPN Overviewdocumentation.
For troubleshooting, please refer to our Troubleshooting Client VPN documentation.
Android
To configure an Android device to connect to the Client VPN, follow these steps:
- Navigate to Settings -> Wireless & Networks -> VPN
- Click the Plus Icon to add an additional VPN profile
Name: This can be anything you want to name this connection, for example, 'Work VPN.'
Type: select L2TP/IPSEC PSK
Server address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
IPSec pre-shared key: Enter the pre-shared key that admin created in Security appliance >Configure > Client VPN settings.
Press save
You will be prompted for user credentials when you connect.
Chrome OS
Chrome OS based devices can be configured to connect to the Client VPN feature on MX Security Appliances. This allows remote users to securely connect to the LAN. This article will cover how to configure the VPN connection on a Chrome OS device. For more information on how to setup the Client VPN feature of the MX or how to connect from other operating systems, please visit the MX documentation.
- If you haven't already, sign in to your Chromebook.
- Click the status area at the bottom of your screen, where your account picture is located.
- Select Settings.
- In the 'Internet connection' section, click Add connection.
- Select Add private network.
- In the box that appears, fill in the information below:
- Server hostname:Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Service name: This can be anything you want to name this connection, for example, 'Work VPN.'
- Provider type: Select L2TP/IPsec + Pre-shared key.
- Pre-shared key: Enter shared secret that admin created in Security appliance >Configure > Client VPN settings.
- Username credentials for connecting to VPN. If using Meraki authentication, this will be an e-mail address.
- Password credentials for connecting to VPN.
- Click Connect.
For more information regarding the configuration of VPN connections in Chrome OS, visit the Google Support page.
To configure an iOS device to connect to the Client VPN, follow these steps:
- Navigate to Settings -> General-> VPN -> Add VPN Configuration...
- Type: set to L2TP.
- Description:This can be anything you want to name this connection, for example, 'Work VPN.'
- Server: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Account: Enter the username
- Password: Enter if desired. If the password is left blank, it will need to be entered each time the device attempts to connect to the Client VPN.
- Secret: Enter shared secret that admin created in Security appliance >Configure > Client VPN settings.
- Ensure that Send All Traffic is set to On.
- Save the configuration.
Meraki Vpn Client Software
macOS
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
The instructions below are tested on Mac OS 10.7.3 (Lion).
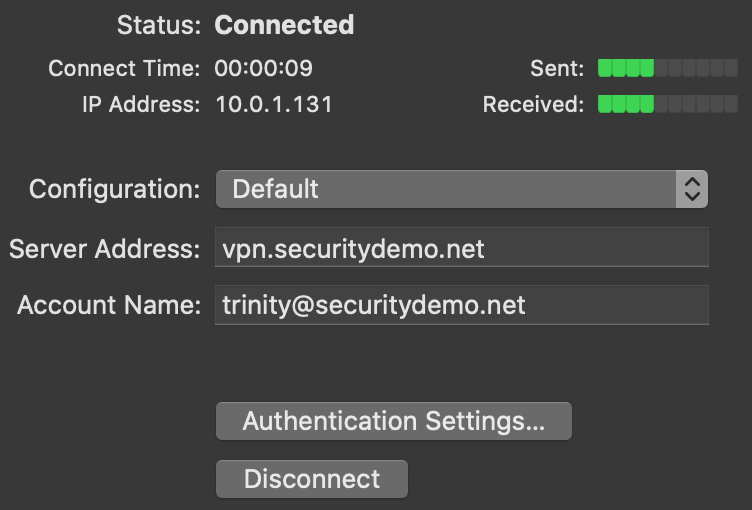
Open System Preferences > Network from Mac applications menu. Click the '+' button to create a new service, then select VPN as the interface type, and choose L2TP over IPsec from the pull-down menu.
- Server Address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Account Name: Enter the account name of the user (based on AD, RADIUS or Meraki Cloud authentication).
- User Authentication > Password: User password (based on AD, RADIUS or Meraki Cloud authentication).
- Machine Authentication > Shared Secret: Enter shared secret that admin created in Security appliance >Configure > Client VPN settings.
The VPN connectivity will not be established if you don't enable the Send all traffic over VPN connection option!
Windows 7
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
Open Start Menu > Control Panel, click on Network and Internet, click on View network status and tasks.
In the Set up a connection or network pop-up window, choose Connect to a workplace (Set up a dial-up or VPN connection to your workplace).
Choose Use my Internet connection (VPN), in the Connect to a workspace dialog window.
In the Connect to a Workplace dialog box, enter:
- Internet address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Destination name:This can be anything you want to name this connection, for example, 'Work VPN.'
Choose 'Don't connect now; just set it up so that I can connect later' option.
Click Next. In the next dialog window, enter the user credentials, and click Create.

Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
Windows 8
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
Open Start Menu > Network and Sharing Center and click Settings.
In the Set Up a Connection or Network pop-up window, choose Connect to a workplace.
(Set up a dial-up or VPN connection to your workplace).
Choose Use my Internet connection (VPN), in the Connect to a Workspace dialog window.
In the Connect to a Workplace dialog box, enter:
- Internet address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- Destination name:This can be anything you want to name this connection, for example, 'Work VPN.'
Go back to Network and Sharing Center and click Change Adapter Settings.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
Windows 10
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, VPN account/user name setting on client devices (e.g., PC or Mac) is the user email address entered in the Dashboard.
Open Start Menu > Search 'VPN' > Click Change virtual private networks (VPN)
From the VPN settings page, click Add a VPN connection.
In the Add a VPN connection dialog:
- VPN provider: Set to Windows (built-in)
- Connection name: This can be anything you want to name this connection, for example, 'Work VPN.'
- Server name or address: Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
- VPN type: Select L2TP/IPsec with pre-shared key
- User name and Password: optional
Press Save.
After the VPN connection has been created, click Change adapter options under Related settings.
Right-click on the VPN Connection from the list of adapters and click Properties.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
In Advanced Properties dialog box, choose 'Use preshared key for authentication' and enter the pre-shared key that admin created in Security appliance >Configure > Client VPN settings.
Back at the Network Connections window, right-click on the VPN connection and click Connect / Disconnect.
Find your VPN profile and click Connect.
Windows XP
Currently only the following authentication mechanisms are supported:
- User authentication: Active Directory (AD), RADIUS, or Meraki hosted authentication.
- Machine authentication: Preshared keys (a.k.a., shared secret).
When using Meraki hosted authentication, use the email address for VPN account / user name.
Open Start Menu > Control Panel, click on Network Connections.
In the Network Tasks section, click on Create a new connection.
Choose Connect to the network at my workplace, in the New Connection Wizard window.
Choose Virtual Private Network connection in the next section.
Then, give a name for this connection. This can be anything you want to name this connection, for example, 'Work VPN.'
Enter the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
In the Connect <Connection Name> box, click on Properties
In the General tab, verify the hostname (e.g. .com)orthe active WAN IP (e.g. XXX.XXX.XXX). Hostname is encouraged instead of active WAN IP because it is more reliable in cases of WAN failover. Admin can find them in Dashboard, under Security appliance > Monitor > Appliance status.
Despite the name 'Unencrypted PAP', the client's password is sent encrypted over an IPsec tunnel between the client device and the MX. The password is fully secure and never sent in clear text over either the WAN or the LAN.
Since Client VPN uses the L2TP over IPsec standard, any Linux client that properly supports this standard should suffice. Please note that newer versions of Ubuntu do not ship with a VPN client that supports L2TP/IP, and will therefore require a 3rd party VPN client that supports the protocol.
Note: The xl2tp package does not send user credentials properly to the MX when using Meraki Cloud Controller authentication, and this causes the authentication request to fail. Active Directory or RADIUS authentication can be used instead for successful authentication.
Configuring Ubuntu 20.04
Ubuntu does not support L2TP VPN by default. You will need to install a couple of software packages to enable this functionality. The instructions below were written for Ubuntu 20.04 LTS with the Gnome desktop environment. Ubuntu versions 16.04 and 18.04 can be configured in a similar manner. However, due to the large number of Linux versions available, it is not feasible to document every supported Ubuntu version.
In order to begin the VPN setup, open up a terminal window. Do this by searching for Terminal in your application list. Click on the Terminal icon to open a new terminal session.
Once the terminal window appears, you will need to enter a few commands.
Meraki Mx Vpn Client Login
Note: You will need to be a part of the “sudoers” group to install these packages. If you receive an error message like “<username> is not in the sudoers file.” you will need to either adjust your permissions, contact your administrator to add your account as an administrator or have them install the software for you.
Once the packages have been installed, you may open up the Network Settings by searching for Settings in the application list, or by clicking on the Network icon at the top right of the screen and selecting Wired (or Wireless) Settings.
Once the Network Settings window pops up, you will see there is a VPN section listed. Click on the + icon to set up a new VPN connection.
Select the Layer 2 Tunneling Protocol (L2TP) VPN type on the modal pop up window. If L2TP is not listed as an option, please see the first step about installing the required packages.
After selecting the L2TP option, a new modal will pop up titled Add VPN. Fill out your VPN Name, Gateway, User name, and Password information here.
Note: To save your password on this screen, you must select the appropriate option from the question mark on the password field.
Next, click on the IPsec Settings button to open the L2TP IPsec Options modal.
Once the modal pops up, expand the Advanced options, and enter the following:
Select OK to continue. You will be returned back to the Add VPN modal. Select the PPP Settings button.
On the L2TP PPP Options modal, select only the PAP authentication method. Be sure the other authentication methods are de-selected. All other options can remain as the default. Select OK to continue.
Select Add at the top right corner of the Add VPN modal to complete the VPN setup.
Now you may connect your VPN by toggling the button on the Network Settings page:
Or by selecting the Connect option from the top right corner menu.
Upon successful connection, a VPN icon will appear next to the network icon in the status bar.
Note: The version of network-manager-l2tp that is installed along with xl2tpd is known to cause issues when connecting to Meraki Appliances. To alleviate this, you must disable the xl2tpd service when using the network-manager GUI to connect to a Meraki VPN.
Meraki Mx Client Vpn Active Directory
To stop the xl2tpd service once use this Terminal command:
sudo service xl2tpd stop
To stop the xl2tpd service for all subsequent reboots use this Terminal command:
Meraki Mx Vpn Client Download
sudo update-rc.d xl2tpd disable
